Cyber Security for Perverts
By: Alex McGeorge
Presented at: Black Rose Tuesday Education, 10/22/13
Version: 3.0
Warnings and such
- I can not answer questions about corporate computer security due to an agreement with my employer
- This presentation is not aimed at IT professionals, though they may enjoy it
- There will be pornography
- There will be gifs!
- A link to this presentation and the handout will appear at the end
- Tested Browsers: Firefox, Google Chrome, YMMV
Notes for the online version
Unfortunately I can't include every single thing I might think of saying when giving this presentation in person, in the online version. I'm making it available as a reference for those who've seen it in person. If you're viewing this online without having seen the presentation some information will be disjointed, such is life. If possible I may try to get a recording of the presentation put somewhere online for reference.
An Important Note: Don't be Evil

Courtesy of Shmorky: butthug.com
Who am I?

The First Law Of Security
If someone wants to fuck you bad enough, they will find a way to make it happen
So what now?
You can improve your security posture such that only the most motivated and most skilled can affect you.

But you can't beat everyone
FetLife
By in large FetLife takes your privacy seriously*
- Both on-site and off-site resources are served over an encrypted channel
- They clearly care about security and privacy from the code we can see
- Hooray!
* I have not done an exhaustive security audit, these are my general impressions
Hot Pix
This is my account's picture page as seen in Google Chrome
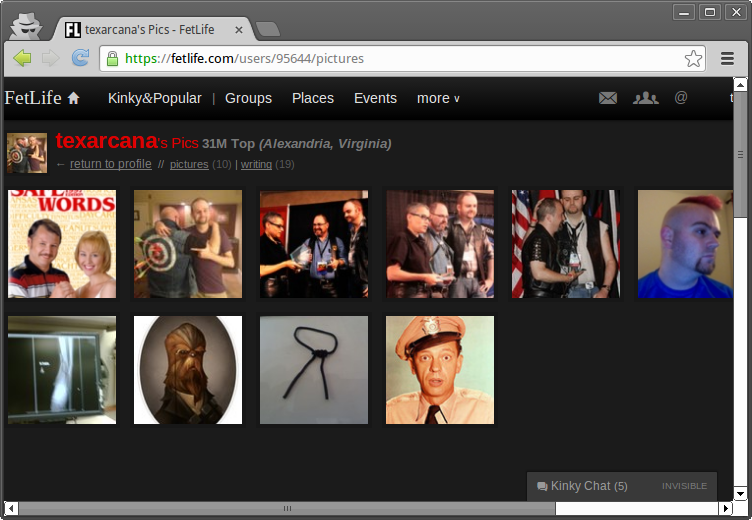
Let's take a closer look at one of the pictures using the 'Inspect Element' function
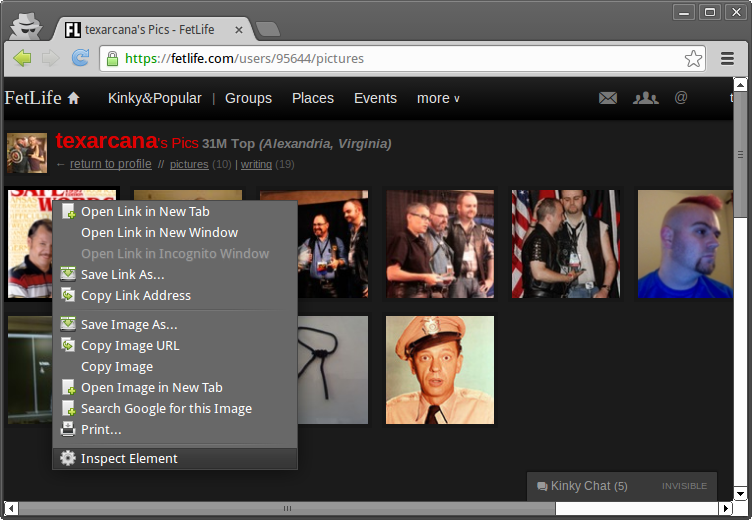
What's the URL for one of my pictures?
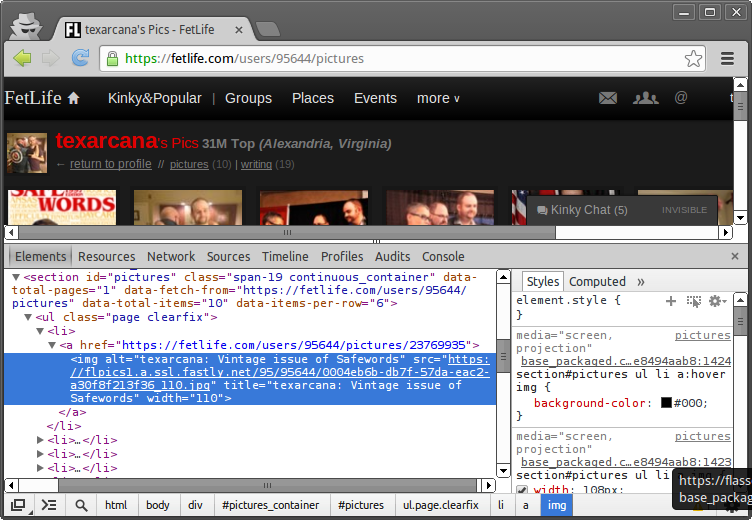
Here's the whole URL:
https://flpics1.a.ssl.fastly.net/95/95644/0004eb6b-db7f-57da-eac2-a30f8f213f36_110.jpg
- https:// - Schema, tells your browser how to connect
- flpics1.a.ssl.fastly.net - Site*, tells your browser WHERE to connect
- /95/95644/ - Path, where to find the file on the site, note 95644 is my FetLife user number
- 0004eb6b-db7f-57da-eac2-a30f8f213f36_110.jpg - File we want to access, this is (probably) random
* URL parsing is actually very complex so I've simplified it. For more check out The Tangled Web by Zalewski.
Ok great, so what?
We know how to connect, the site where FetLife pictures live and how to find where on the site all the user's pictures live
Not really so bad
- There's not a straight forward way to list the pictures in a given directory
- And we don't have a good way to predict those (probably) random file names
The catch
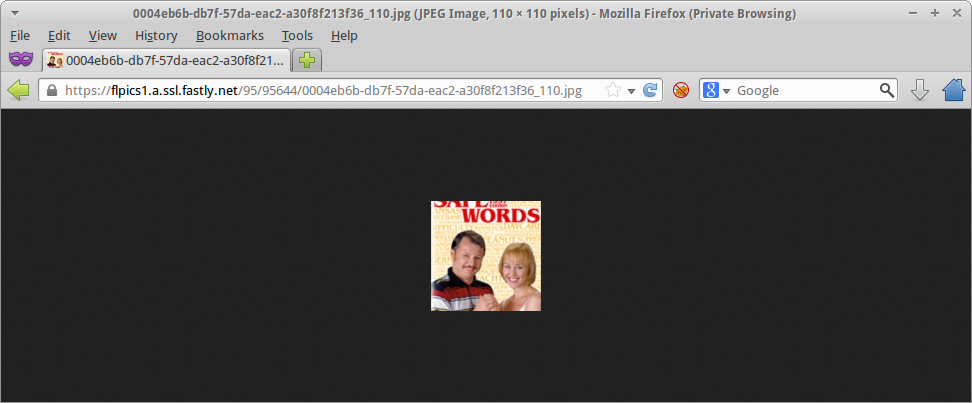
Miss it?
- I'm accessing this picture directly from a different browser that is not logged in
- That means if I know the address of the picture I can see it whenever I want without authentication
- These addresses never (to my knowledge) change
Security Updates
(Sections: 1.1, 2.1, 3.1, 4.3, 5.1)
Definitions
- Bugs - Errors in software
- Vulnerability - A bug with some type of security consequence
- Exploit - A program written to take advantage of a vulnerability in another piece of software
- 0day - A vulnerability (and sometimes exploit) that is known privately but not disclosed publicly
- Malware - Any type of software that intends to maliciously and persistently alter the normal operations of your computer
How to Think of Software
It can take many kinds of input and preform many kinds of actions

Image courtesy of GitaaOnline: here
Basic Binary Entomology
Unexpected input => Software Bug =>Basic Binary Entomology Pt. II
Sometimes these bugs allow for control of execution which can avoid a crash but make the software behave in a way the attacker chooses

Image courtesy of Squ11head: Deviant Art
Summary
Do I need to apply this security update?

Erotic photo break!

Anti-Virus
Realistic Expectations
- Anti-Virus will be less effective at preventing attacks
- Anti-Virus will be more effective at cleaning up
- Do I need anti-virus for my Mac? Probably
I'm compromised!
(General guidelines)
- Take the computer off your network
- When you need to update or install AV or anti-malware, take other computers off the network
- Using a separate uninfected computer change all your passwords
- If you have done online shopping from the infected computer, notify your bank/credit for suspicious charges
- Keep rescanning with AV and anti-malware until you receive a clean bill of health, reboot between scans
- Always maintain good backups! Sometimes you have to start from scratch
Links
AV-Test.org - For comparissons of popular AV software
VirusTotal.com - Scan files with most major AV products
Summary
- Pick an AV product that annoys you the least and is well reviewed
- Set up weekly scans
- Set it to auto-update itself
Firewalls
Sections: 1.3, 2.2
A firewall analogy

Switchboard image courtesy of Library of Congress Collection
Summary
- Think of a port as an extension on a switch board
- Programs listen on a specific port
- Firewalls are like operators, they allow or disallow connections based on a set of rules
- While important, they are becoming less of a complete solution with the advent of 'clientside' exploits
- All modern operating systems have good builtin firewalls
The unfriendly network
Section 3.2
Man-in-the-Middle

Someone is getting fucked
Wireless, how does it work?
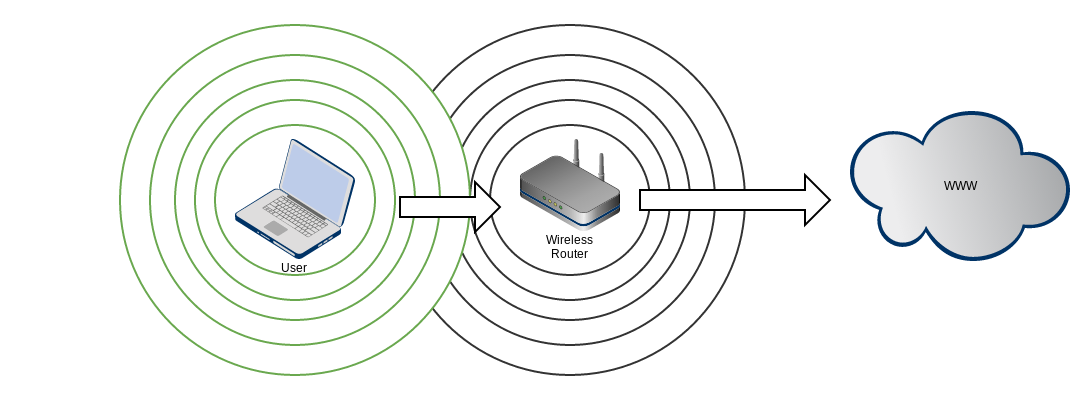
An attacker enters!
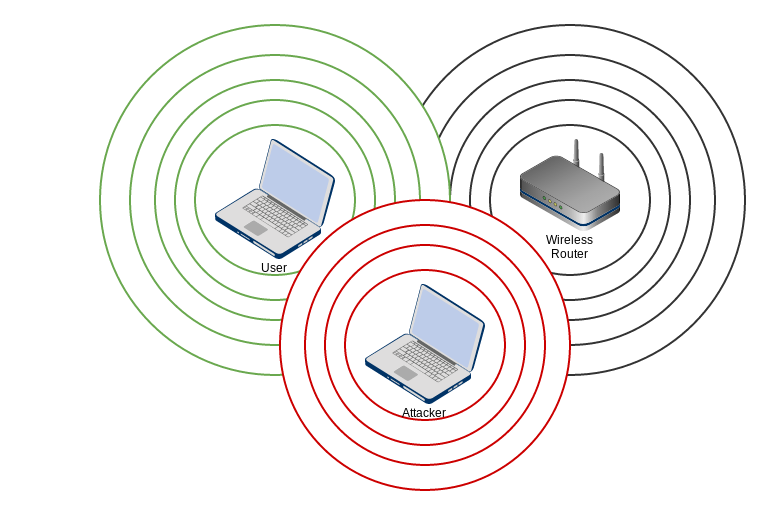
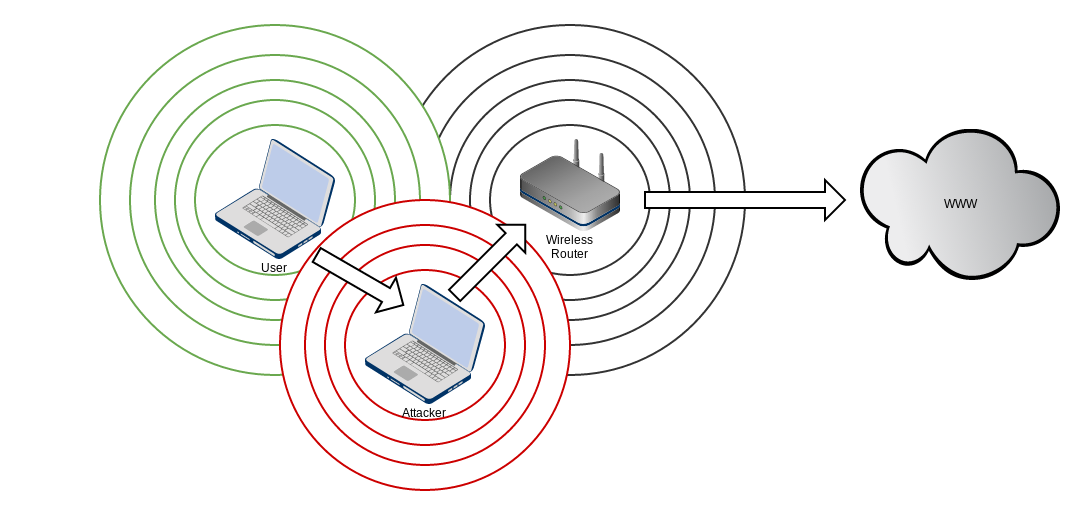
An attack!
6 Degrees of Kevin Beacon

Image courtesy of Google TV
Summary
- By design phones will attempt to connect to networks they've seen before
- This can provide information about where you hang out
- Attackers can choose to impersonate these networks to trick your phone into connecting
- Onces you're connected to an attacker controlled network they can see, intercept and modify your traffic
- Encryption is the solution to this problem
Encryption
The cause of and solution to many of life's problems
VPN Example
- You're at Starbucks and want to check your mail so you fire up the VPN
- You make the connection to the VPN server
- Since the VPN server isn't also your mail server, it forwards your mail traffic back to the internet
VPNs
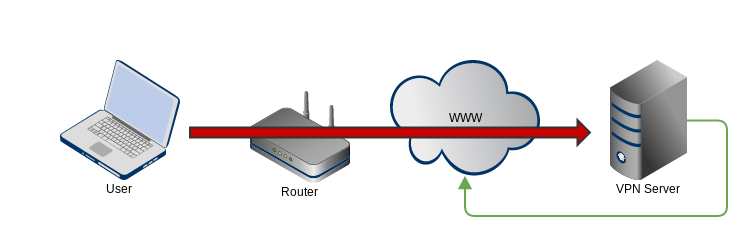
The red line represents your secure connection to the VPN server
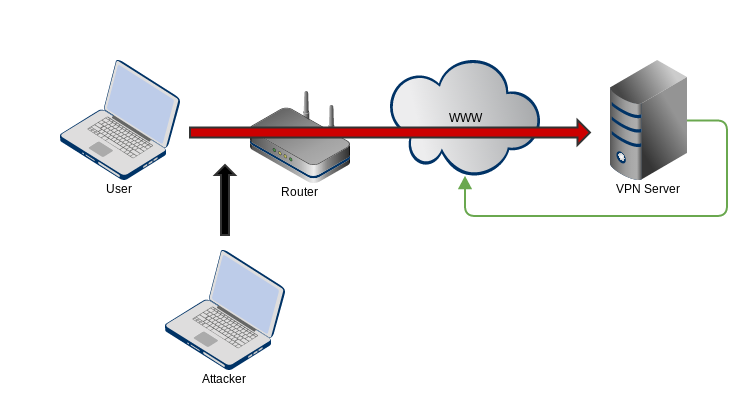
Attackers1 can see where you are connected but not what you are doing
Who are not state sponsored
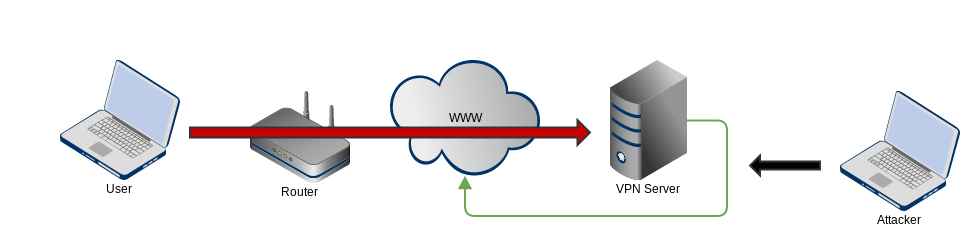
Traffic that leaves the VPN server to route back to the internet is not protected by the VPN
VPN Summary
- VPNs provide an encrypted tunnel between you and the VPN server
- This means that your connection to the server is protected
- If the VPN server then forwards your traffic to another site (i.e. Google) it is not protected after it leaves the VPN server
- Use SSL (https) to protect your traffic in this instance
SSL
- An encryption technology typically used to secure web connections
- Relies on a "chain of trust" to establish that the server and the certificate authority are in fact who they claims to be
- The math is good but there are attacks against the implementation
Practical SSL
- Whenever you are providing presonal information ensure you are accessing the site via SSL (look for https:// in the URL)
- The EFF's HTTPS Everywhere browser plugin does a good job of forcing you to do this
- Be mindful that SSL only protects your data in transit, if an attacker has hacked the web server they can see the data
Protecting your Data at Rest
At rest?
- The encryption technologies we've talked about thus far are for protecting your data while it is in transit
- Protecting your data when it reaches its final destination requires another type of product
TrueCrypt
- Free and cross platform (Windows/Mac/Linux)
- Uses good encryption in the default choices
- Choose a complex password different than any you use elsewhere
- Use it to protect backup devices and personal sensitive data
Wireless Networks
Sections: 4.X
Wireless, how does it work?

Wireless Authentication Schemas
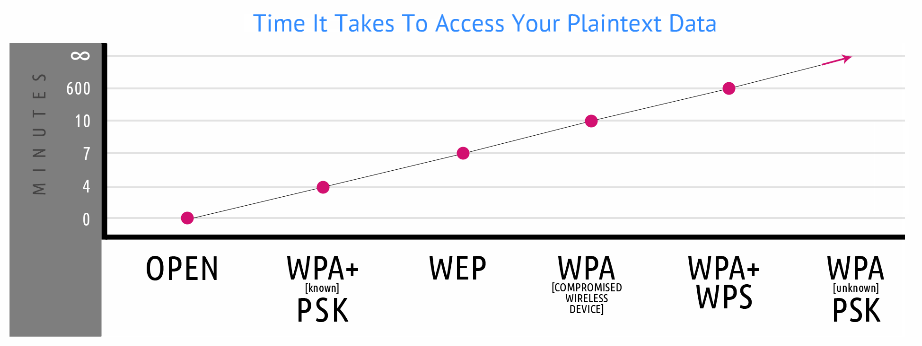
Image Courtesy of Secrets in your Pocket presentation
Attacks against the router itself

From Office Space
Manufacturer Default Passwords
Summary
- WPA2 based authentication is the current secure standard
- WEP and WPS are both broken, disable them
- Your router needs updating too
- Change the default passwords on the router
- Change your wireless keys once every 6 months
The Browser
- The browser parses many types of data
- It's relatively easy to trick or force someone to view something you control
- Unexpected input => software bug => :(
Browser Extensions
- Additional software to render specific content
- Java
- Flash
- Acrobat
- Office Suites
So the sky is falling, now what?
- No browser is perfect but I like Chrome
- Good security developers
- Good memory protection and privilege separation
- Mandatory updates
- Security bug bounties
- Not perfect: (ex: Pwn2Own Contest)
- Disable as many browser extensions as possible
- Uninstall Java
Browser extensions that can help
- EFF's HTTPS Everywhere (FFX, Chrome)
- Flash Block (FFX), Flash Control (Chrome)
- No Script (FFX), Chrome can do this natively
- Ghostery (All major browsers)
What does private browsing actually do?
Make it slightly harder for your S/O to look at your porn history

The Road to El Dorado
Erotic photo break!

Kristin Scott Thomas via Dorothy Surrenders
Erotic photo break!
 Iggy Pop via Dior
Iggy Pop via Dior
Privacy
An enormously deep rabbit hole
Caveats
Good news!
If you are reading this or attending this lecture, you are almost definitely not a priority intelligence target. The NSA does not care what you jerk off to.
Bad news
Even if we spent the entire 90 minutes of this talk discussing privacy, I would be unable to impart enough knowledge for you to avoid being spied upon
by a state sponsored adversary.
Choices
If you're chosing adversaries, choose someone other than the NSA
Realistic choices
| Desire | Difficulty |
| I don't want other people using this network knowing what I'm doing | Easy |
| I don't want my ISP knowing what I'm doing | Easy |
| I don't want local law enforcement knowing what I'm doing | Difficult |
| I don't want federal law enforcement knowing what I'm doing | Very difficult |
| I don't want NSA or allied intelligence agencies knowing what I'm doing | Incredibly difficult |
Tor
 Brought to you by =>
Brought to you by =>

Privacy Links
These can get pretty technical but the information is solid
- The Grugq's Tumblr Blog (Very technical)
- The Grugq's GitHub Blog (Very technical)
- Bruce Schneier's Blog (Less technical)
- Matthew Green's Blog (Very technical)
- Kreb's on Security (Less technical)
- Electronic Frontier Foundation (Less technical)
Credits and Locations
Written by: Alex McGeorge
http://fapsec.net/csfp/index.html - (Presentation)
http://fapsec.net/csfp/CSFP_Outline.pdf - (Outline)
Made with -> Reveal.js
HTML Presentations Made Easy
Created by Hakim El Hattab / @hakimel
